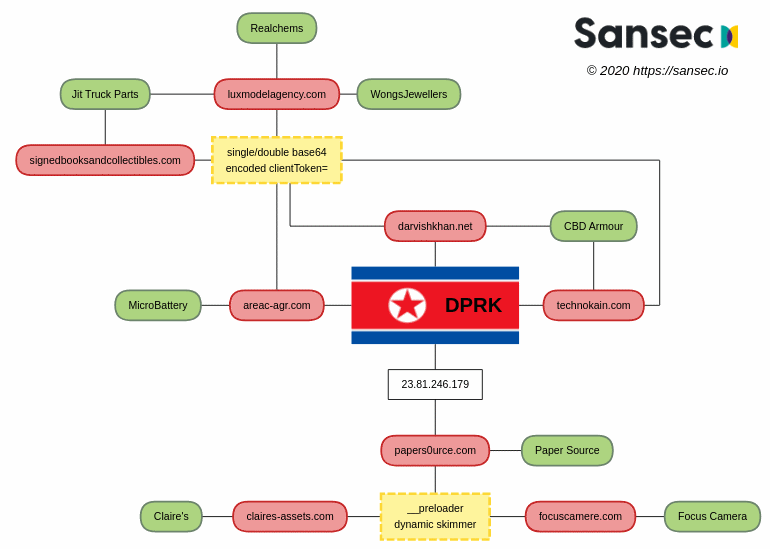
North Korean Hackers Linked to Magecart Attacks on US Stores
Key: Green = hacked store Red = Hidden Cobra controlled exfiltration nodes Yellow = Unique technique linking the attacks and malicious code A report by SanSec, a Dutch security firm published a report today in which the phishing attacks were linked to North Korean Hackers, Lazarus group in particular. Such forms of attacks are called “internet skimming,” “e-skimming,” or “Magecart attack,” with the last name coming from the name of the first organization that went through such tactics. The Magecart attacks might be simple to look at but the attacks require some serious Hacking Skills to execute. The main goal of the hackers is to gain control of the backend servers of the organization, in which they can run the malicious code in the frontend of the website. The code remains invisible as it only loads up on the checkout page, logs the Payment details of the victim, then the data is sent to a remote server and is sold in the dark markets for a considerable amount of money. The sitting targets include accessories giant Claire’s, Wong’s Jewellers, Focus Camera, Paper Source, Jit Truck Parts, CBD Armour, Microbattery, and Realchems. The list is much larger with the inclusion of dozen of stores. “How HIDDEN COBRA got access is yet unknown, but attackers often use spearphishing attacks (booby-trapped emails) to obtain the passwords of retail staff,” says SanSec founder Willem de Groot. HIDDEN COBRA is another moniker for the Lazarus group given by the US Department of Homeland Security to North Korea’s elite state-operated hacking crews. These North Korean Hackers usually hack to raise money for the illegal armament plans of North Korea, which has been placed under huge sanctions by the UN. These are the same hackers who were blamed for the WanaCry Ransomware.